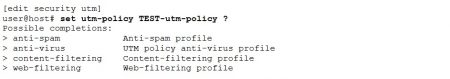
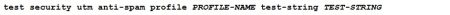Unified Threat Management (or short UTM) belongs to the advanced security capabilities on all SRX devices (support for high-end devices is from 12.1X46 release). Following features are members of the UTM:
- antispam (Local or with Spam Block server)
- antivirus (Kaspersky also called Full, Sophos, Juniper Express)
- web filtering (Juniper Enhanced, Local, Surf-Control Integrated, WebSense redirect)
- content filtering
Please note the list above applies to Junos release 12.1X47. In older Junos releases some feature options (for example Juniper Enhanced web filtering) might not be available as they were introduced later.
All UTM processing is applies to only following protocols - HTTP, FTP, SMTP, POP3 and IMAP – and no other. To make traffic subject to UTM inspection it needs to be permitted by a security policy first. In other words the UTM policies is referenced within the security policy permit action. This is no different as with other advanced security features such as IDP and AppFW.
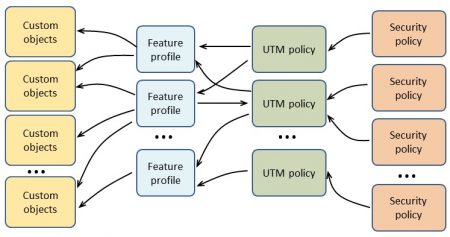
The UTM configuration is based on the following elements:
- custom objects
- feature profiles
- UTM policy
The image below illustrates their relationships and the relationship between UTM policy and security policies.
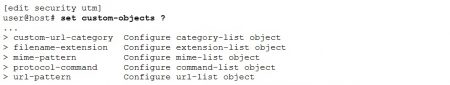
Custom objects (as the name indicates) are the means to provide custom values to the UTM configuration. They help to tune and tweak the UTM so it operates as desired. Please keep in mind they are completely optional. In some cases it can even happen they do not appear in the UTM configuration at all. Furthermore they add flexibility to the UTM configuration because each defined custom object can be reused multiple times. For example the same url-category object can be referenced from the anti-virus and from web-filtering.
The list below displays the available custom object types:
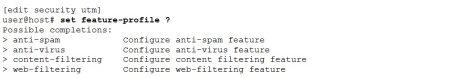
On the other hand feature profiles are mandatory. For each UTM feature to operate a respective feature profile is required. Following feature profiles exist in the UTM configuration.
As presented on the first image the custom objects are references from within the feature profiles.
The last UTM element is the UTM policy. It combines feature profiles to be used to inspect the traffic. The UTM policy itself is then referenced from the security policies permit action. Junos allows multiple UTM policies to coexist on a single device. The structure of the configuration offers great flexibility. Each security policy can reference different UTM policy. In turn each individual UTM policy can reference different set of features and their profiles. And essentially different or same custom objects can be used by different feature profiles. For example one security policy can reference an UTM policy that has associated only the anti-virus feature while second security policy can have linked an another UTM policy that contains anti-spam and two different content filtering profiles (one for HTTP and the other for FTP traffic).
The complete reference hierarchy of feature profiles within an UTM policy:
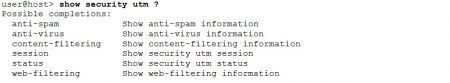
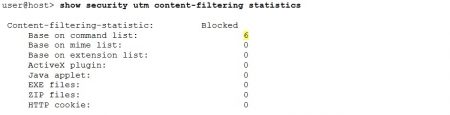
The Junos operational mode “show security utm” command provides information suitable for quick status check and basic monitoring of the UTM operation. For example the “show security utm status” and “show security utm sessions” commands display whether UTM is running or not and display information about the UTM sessions (maximum, active, freed and allocated). The feature names can be used as command parameters. If defined the command output displays either status or statistics (specified by the next command parameter) of the particular feature.
Few example commands and outputs are presented below:
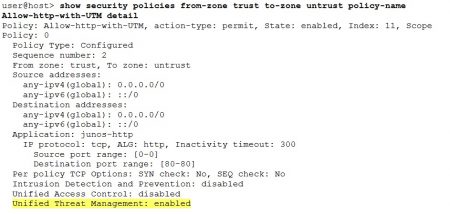
When troubleshooting UTM is it always good to double check whether the security policy has the UTM enabled. Even though the UTM might correctly configured no traffic will be inspected if the association from the permit action is missing. Also please note the command output shows only whether UTM is enabled in the security policy or not. It does not display the linked UTM policy. For that the configuration file has to be consulted.
Additionally an operational mode command for testing the anti-spam, anti-virus and web-filtering features is available. The command syntax is:
An example how to use the testing command:
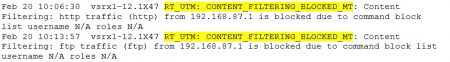
When the UTM performs an action (such as blocking, tagging, etc.) a syslog message is generated. The messages are easy to identify just look for the “RT_UTM“ string.
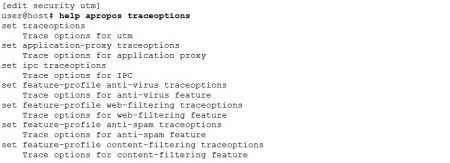
Traceoptions are provided for deeper UTM investigation and troubleshooting. Several traceoptions exists for UTM – on per feature basis, for the IPC (inter process communication), application proxy and generally for UTM.
Each traceoption above allows only to define the flags. The possibility to define custom trace file name is not available and system uses the predefined files:
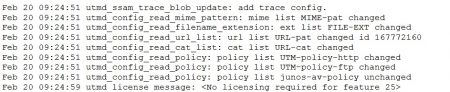
The messages about the processing of the UTM configuration (modifications, additions and deletions) are a quite substantial part of the /var/log/utmd. Here are few examples of such entries.
Going further. The insight into actual data processing is provided by the security flow traceoptions provide. They reveal if the traffic has been processed by the UTM or not. The UTM processing is done through plugins.
The example below shows the trace messages for such case. (For brevity only relevant messages are listed.)
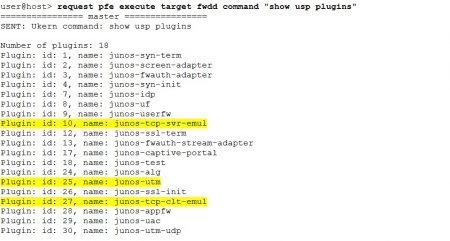
To shed some light on the plugin processing here are the mappings between plugins and their IDs:
The security flow traceoptions messages indicate the traffic was processed by the plugins 10 (junos-tcp-svr-emul), 27 (junos-tcp-clt-emul) and most importantly 25(junos-utm). The junos-tcp-svr-emul and junos-tcp-clt-emul plugins are used by the TCP proxy (one emulates server and the other the client side in the TCP connection).
Conclusion
The UTM features – anti-spam, anti-virus, content and web filtering – belong to the advanced security capabilities on SRX. This blog was focused on the UTM functionality in general. It starts with the description of the configuration elements and their relationships. And the rest of the article deals with the options for UTM monitoring (operational mode commands) and troubleshooting (UTM and security flow traceoptions).