Demo – Network Configuration Compliance Check (NSO)
Diagram:
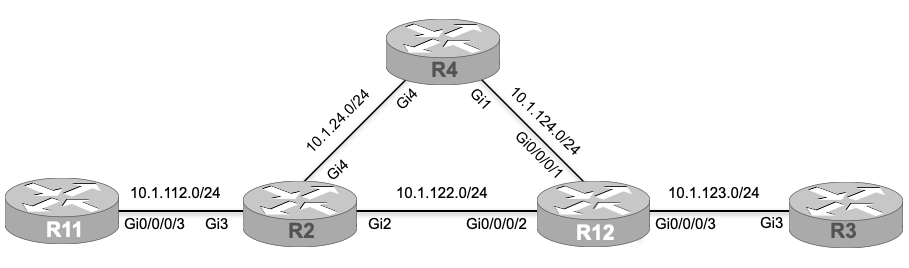
(For this lab, you need to load the initial configuration named “lab80-initial” onto the devices before going through the task lists. The final configuration/solution for this lab (lab80-final) can also be loaded onto the devices. For more information about accessing our labs and/or loading the configuration to the devices, please refer to the lab instructions section in the course introduction chapter.)
Tasks:
- Create a compliance check template to validate the minimal configs like name servers, syslog, NTP in it. Template should be applicable for both IOS XE and IOS XR.
- name-servers : 8.8.8.8, 9.9.9.9
- NTP server : 10.10.254.201
- Syslog server : 10.10.254.201
- Run the compliance template to generate report in text format.
- Resolve all the descripencies from the compliance check report.
Technology Overview:
In order to maintain the standard of configuration, we can use Cisco NSO for the compliance validation for both IOS XR and XE devices.
Detailed Explanation:
To minimize the administrative overhead caused by manual verification and the configuration, we can utilize Cisco NSO to create a compliance template where we can define a set of configurations and run the template to validate against the running configuration of the routers. Based on the report generated by the check, configurations of discrepant devices can be updated at once. The set of configurations should be created on the basis of software like IOS XE, IOS XR, etc. The device group created in earlier labs can be used to validate the compliance on the host devices.
Configuration:
As discussed above, the configuration section should include the device group and the compliance template as the major components. Based on what we have been given in the task lists, two name-servers, logging server followed by NTP server need to be defined within compliance template. Another task is to generate reports in text output format as we have HTML and XML as alternatives. Once we run the compliance validation and if the system finds differences in the configuration, it will notify us with compliance status as “violation”. If there is no discrepencies, the “no-violation” status is displayed.
automation:
ncs_cli -C
config
devices template COMPLIANCE-CHECK
ned-id cisco-ios-cli-6.69
config
ip name-server name-server-list 8.8.8.8
!
ip name-server name-server-list 9.9.9.9
!
logging host ipv4 10.10.254.201
!
ntp server peer-list 10.10.254.202
!
!
!
ned-id cisco-iosxr-cli-7.33
config
logging host 10.10.254.201 default
!
domain name-server 8.8.8.8
!
domain name-server 9.9.9.9
!
ntp server server-list 10.10.254.202
!
!
!
!
commit
!
top
!
compliance reports report COMPLIANCE-CHECK
compare-template COMPLIANCE-CHECK CISCO
commitExecute the use case. To run compliance report.
compliance reports report COMPLIANCE-CHECK run outformat textBy default, the report is generated in XML format. For text report compliance reports report COMPLIANCE-CHECK run outformat text. For HTML report compliance reports report COMPLIANCE-CHECK run outformat html.
id 1
compliance-status violations
info Checking 5 devices and no services
location file://automation//var/opt/ncs/state/compliance-reports/report_1_ccie_1_2021-12-23T17:16:32:0.textThe compliance report in the text format looks as below.
[root@automation ~]# more /var/opt/ncs/state/compliance-reports/report_1_ccie_1_2021-12-23T17\:16\:32\:0.text
reportcookie : g2gCbQAAAABtAAAAEENPTVBMSUFOQ0UtQ0hFQ0s=
Compliance report :
Publication date : 2021-12-23 17:16:32
Produced by user : ccie
Chapter : Summary
Compliance result titled "" defined by report "COMPLIANCE-CHECK"
Resulting in violations
Checking 5 devices and no services
Produced 2021-12-23 17:16:32
From : Oldest available information
To : 2021-12-23 17:16:32
Template discrepancies
COMPLIANCE-CHECK
Discrepancies in device
R11
R12
R2
R3
R4
Chapter : Details
Template discrepancies details
COMPLIANCE-CHECK
Device R11
config {
domain {
+ # after name-server 1.1.1.1
+ name-server 9.9.9.9;
}
ntp {
server {
+ server-list 10.10.254.202 {
+ }
}
}
}
Device R12
config {
domain {
+ # first
+ name-server 8.8.8.8;
+ name-server 9.9.9.9;
}
ntp {
server {
+ server-list 10.10.254.202 {
+ }
}
}
}
Device R2
config {
ip {
name-server {
+ # after name-server-list 1.1.1.1
+ name-server-list 9.9.9.9;
}
}
logging {
host {
+ ipv4 10.10.254.201 {
+ }
}
}
ntp {
server {
+ peer-list 10.10.254.202 {
+ }
}
}
}
Device R3
config {
ip {
name-server {
+ # first
+ name-server-list 8.8.8.8;
+ name-server-list 9.9.9.9;
}
}
logging {
host {
+ ipv4 10.10.254.201 {
+ }
}
}
ntp {
server {
+ peer-list 10.10.254.202 {
+ }
}
}
}
Device R4
config {
ip {
name-server {
+ # first
+ name-server-list 8.8.8.8;
+ name-server-list 9.9.9.9;
}
}
logging {
host {
+ ipv4 10.10.254.201 {
+ }
}
}
ntp {
server {
+ peer-list 10.10.254.202 {
+ }
}
}
}The “first” indicates that the name-server is to be added onto the host device with name-server configured while the “after” replaces configured parameter as per compliance template.
To resolve compliance discrepencies, compliance template can be applied to the device group using following commands.
automation:
ncs_cli -C
config
devices device-group CISCO apply-template template-name COMPLIANCE-CHECKAs soon as the command is run on the NSO, we can see the following output.
apply-template-result {
device R11
result ok
}
apply-template-result {
device R12
result ok
}
apply-template-result {
device R2
result ok
}
apply-template-result {
device R3
result ok
}
apply-template-result {
device R4
result ok
}Use these commands to see the proposed changes to the network to bring the devices in compliance using the “native” device-type CLI.
commit dry-run outformat nativeThe above command gives the following output.
native {
device {
name R11
data domain name-server 9.9.9.9
ntp
server 10.10.254.202
exit
}
device {
name R12
data domain name-server 8.8.8.8
domain name-server 9.9.9.9
ntp
server 10.10.254.202
exit
}
device {
name R2
data ip name-server 9.9.9.9
logging host 10.10.254.201
ntp server 10.10.254.202
}
device {
name R3
data ip name-server 8.8.8.8
ip name-server 9.9.9.9
logging host 10.10.254.201
ntp server 10.10.254.202
}
device {
name R4
data ip name-server 8.8.8.8
ip name-server 9.9.9.9
logging host 10.10.254.201
ntp server 10.10.254.202
}
}Commit the configuration, which will have NSO send the commands to the devices and make them compliant.
commitExit config mode and re-run the compliance report, so NSO verifies that what is on the device is in compliance with the defined template.
end
compliance reports report COMPLIANCE-CHECK run outformat text
ccie@ncs# compliance reports report COMPLIANCE-CHECK run outformat text
id 2
compliance-status no-violation
info Checking 5 devices and no services
location file://automation//var/opt/ncs/state/compliance-reports/report_2_ccie_0_2021-12-23T17:36:25:0.text
ccie@ncs#
Verification:
The “no-violation” compliance status indicates that the discrepancies do no longer exist on the host devices. However, we can log into the host devices and check the running configuration as part of the final verification.
R2#sh run | sec name-server|logging|ntp
ip name-server 8.8.8.8 1.1.1.1 9.9.9.9
logging host 10.10.254.201
ntp server 10.10.254.202
R3#sh run | sec name-server|logging|ntp
ip name-server 8.8.8.8 9.9.9.9
logging host 10.10.254.201
ntp server 10.10.254.202
R4#sh run | sec name-server|logging|ntp
ip name-server 8.8.8.8 9.9.9.9
logging host 10.10.254.201
ntp server 10.10.254.202
RP/0/RP0/CPU0:R12#sh run name-server
Fri Dec 24 08:34:41.452 UTC
domain name-server 8.8.8.8
domain name-server 9.9.9.9
RP/0/RP0/CPU0:R12#sh run ntp
Fri Dec 24 08:34:51.867 UTC
ntp
authenticate
trusted-key 1
server vrf MGMT 10.10.254.201
server vrf MGMT 10.10.254.202
server 10.10.254.202
update-calendar
!
RP/0/RP0/CPU0:R12#sh run logging
Fri Dec 24 08:34:56.490 UTC
logging console disable
logging monitor disable
logging buffered 125000000
logging buffered informational
logging 10.10.254.201 vrf default severity info port default
logging 10.10.254.202 vrf default severity info port default
logging source-interface Loopback0
logging suppress duplicates